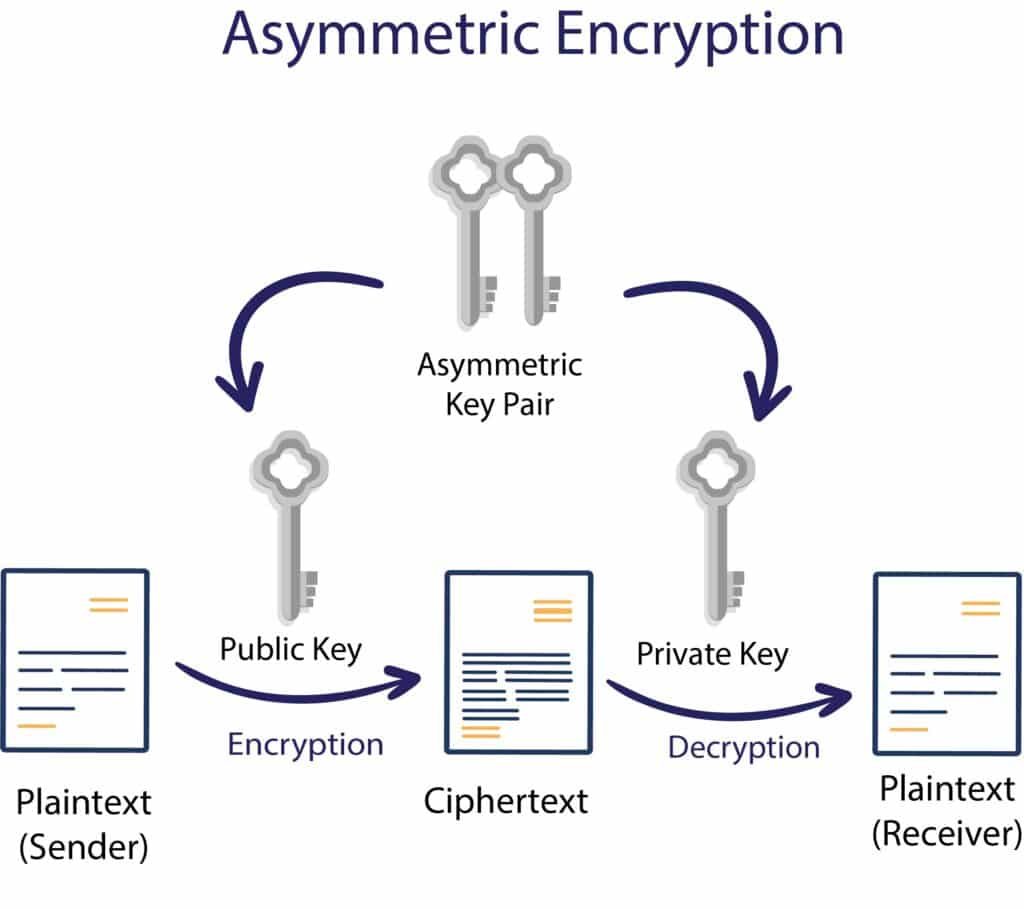
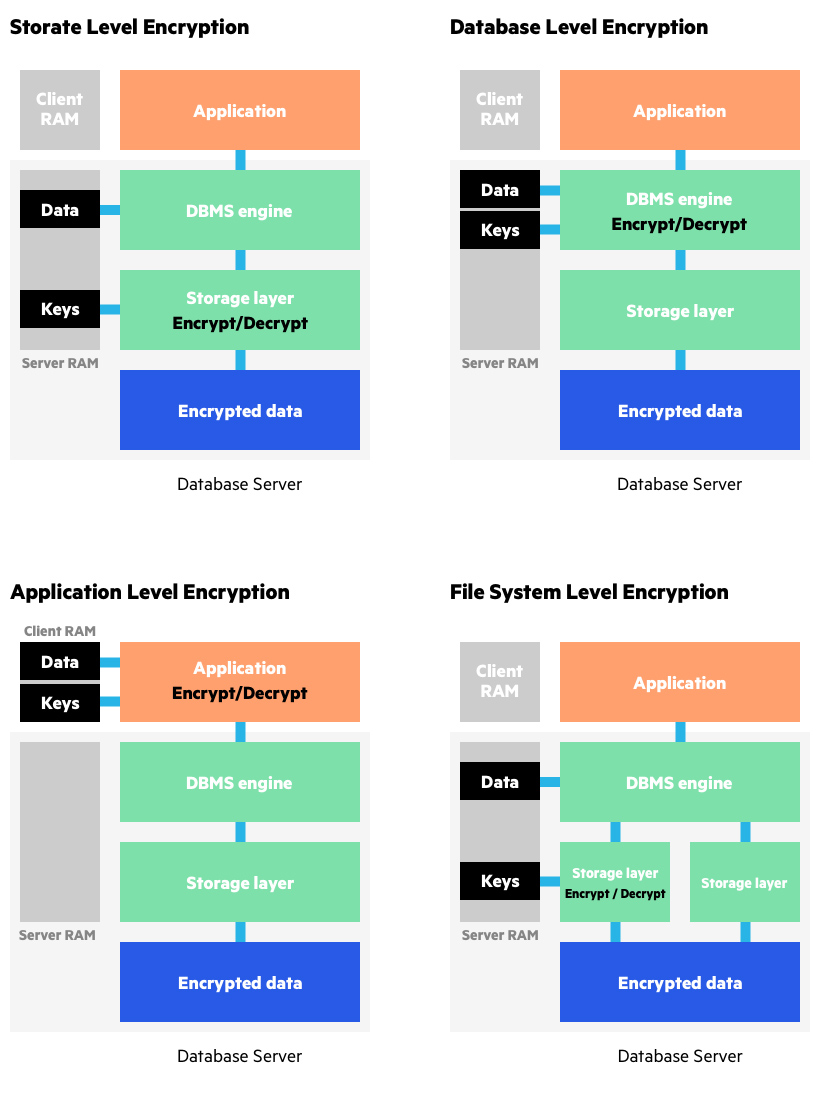
What is Cryptography in security? What are the different types of Cryptography? | Encryption Consulting
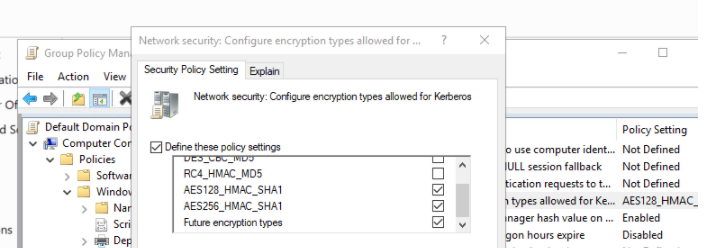
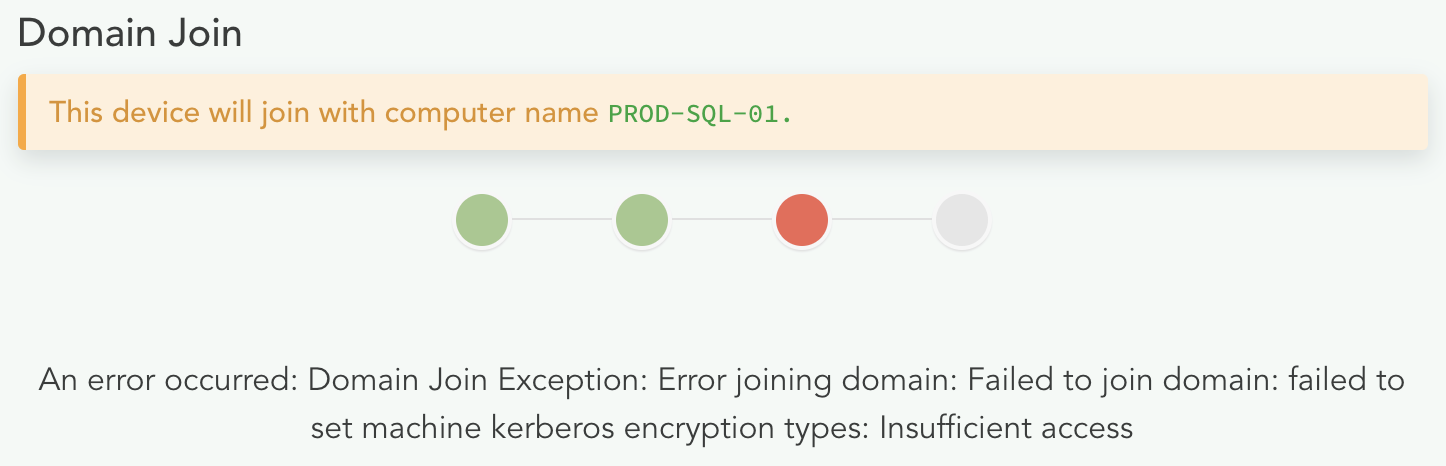
Changing encryption methods (ciphers) for accessing SmartConsole using Active Directory Authentication

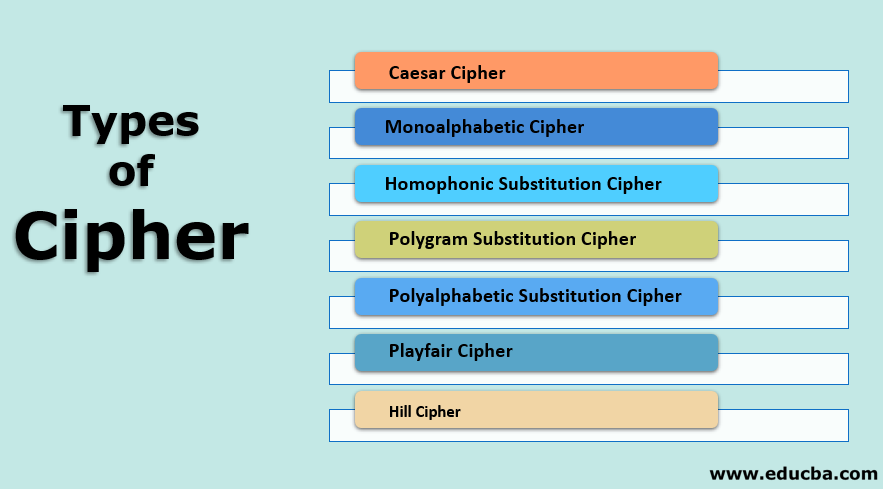
Types of Encryption: 5 Encryption Algorithms & How to Choose the Right One - Hashed Out by The SSL Store™

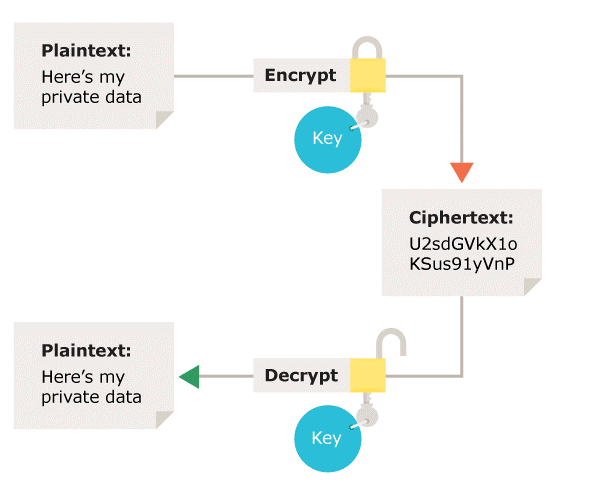


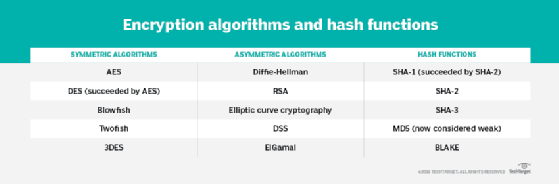
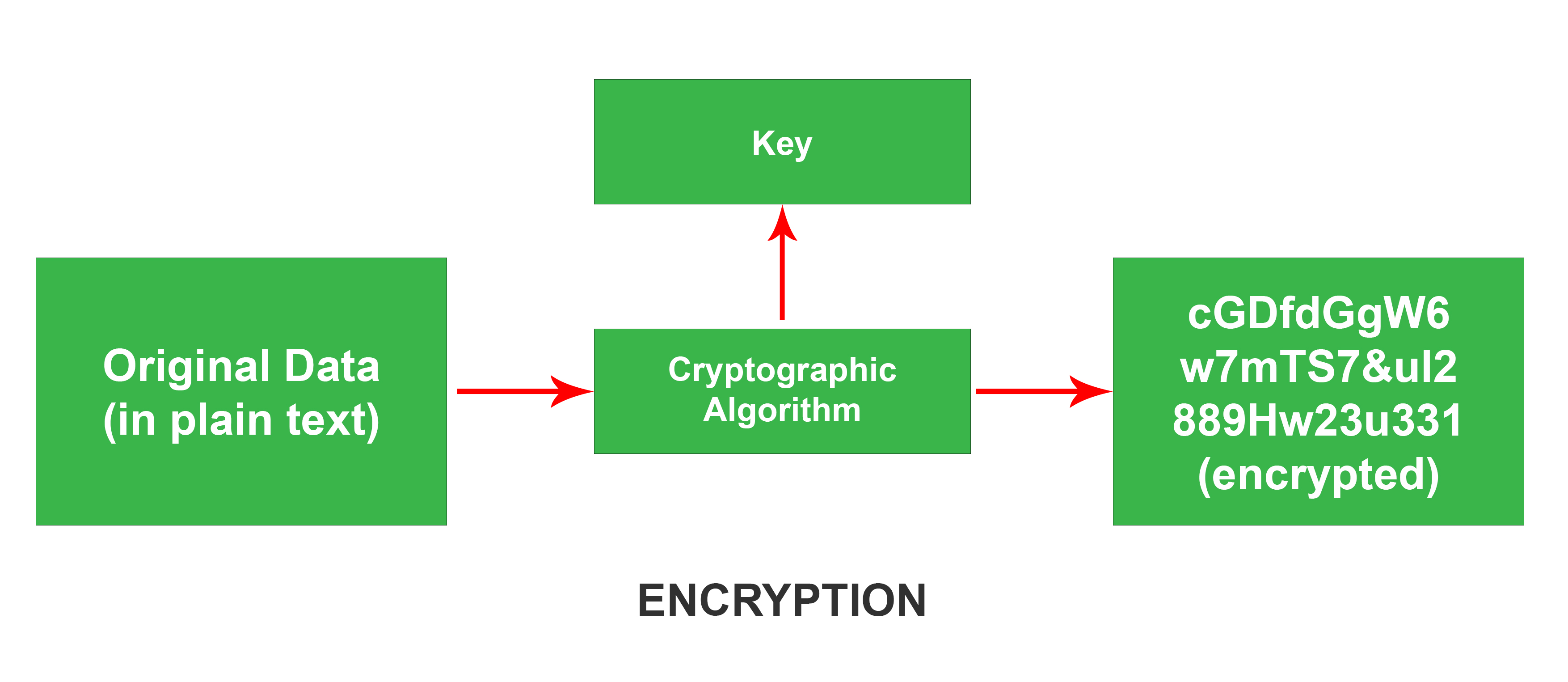


![Review] 3 Main Types of Encryption: Hash, Symmetric, Asymmetric | by Peter Chang | Medium Review] 3 Main Types of Encryption: Hash, Symmetric, Asymmetric | by Peter Chang | Medium](https://miro.medium.com/max/640/1*23RpkZuWAeSP7x0YdMtsdQ.png)

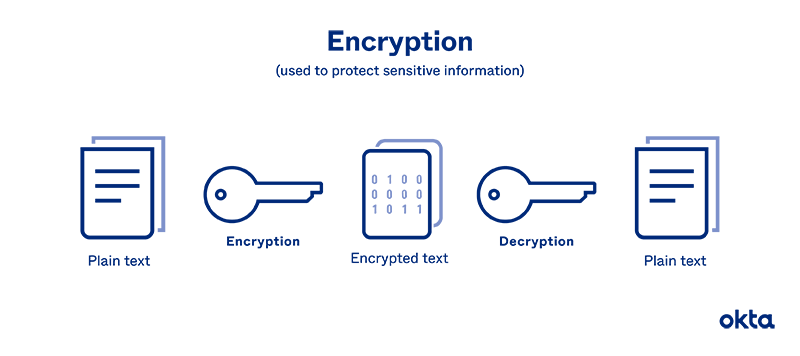








![What Is Data Encryption: Algorithms, Methods and Techniques [2022 Edition]| Simplilearn What Is Data Encryption: Algorithms, Methods and Techniques [2022 Edition]| Simplilearn](https://www.simplilearn.com/ice9/free_resources_article_thumb/What_are_the_Most_Effective_Data_Encryption_Techniques.jpg)